Last week there was an attempt to attack and bring down the DNS root nameservers of the Internet with a large-scale distributed denial-of-service (DDoS) attack. The attack caused major problems for at least one of the 13 root nameservers (ironically the one maintained by the U.S. Department of Defense.)
This is not the first time the root nameservers have been under attack. In October 2002, a smaller attack had a much more noticeable effect, with some sources claiming that as many as two thirds of the root nameservers were affected and the whole Internet actually slowed down significantly.
This leads to some important questions: What would happen if an attack on the root nameservers is successful, and why are they so hard to bring down?
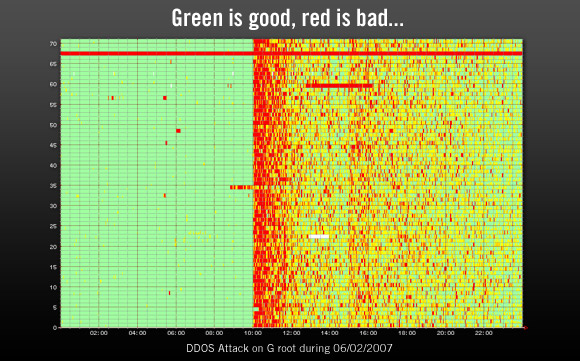
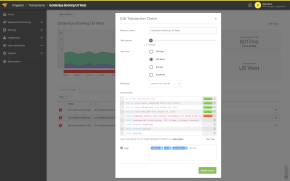
Image: Graph from from RIPE NCC showing the effect of the DDoS attack on the U.S. Department of Defense G root nameserver.
What would happen if all root nameservers stopped working?
An attack on the root nameservers is essentially an attack on the entire Internet since they are necessary for the DNS to function properly. Hypothetically, if all root nameservers stopped working, DNS lookups would gradually start failing. Local DNS servers only cache domain name information for a certain time before they need to contact the root nameservers again.
Within minutes – Some DNS lookups would start failing.
After an hour – A significant number of DNS lookups would be failing.
After a day – Most DNS lookups would be failing.
What happens when DNS lookups stop working? Surfing the Web won’t work anymore. Sending email won’t work anymore. Everything that uses domain names breaks (which means almost everything). You could technically access the Internet, but only using IP addresses. But how would you normally find those IP addresses? Answer: Via the DNS…
It should be pointed out that it’s extremely unlikely that all root nameservers would fail at the same time. Some would say that with the current setup it’s impossible. Which leads us to…
Why are the root nameservers so hard to bring down?
Back in 2002 there were 13 root nameserver locations in four countries. The attack that year made it obvious that wasn’t enough, so since then the number of server locations has been increased significantly. Though the DNS protocol only allows for 13 actual root nameserver addresses, six of these now use a routing protocol called anycast to distribute requests to a large number of different locations. Currently there are 123 globally distributed root nameserver locations. (An up-to-date list can be found at www.root-servers.org.)
This decentralization of the root nameservers has made them very hard to attack even with a large-scale distributed attack such as the one from last week since any attack is automatically diluted and spread out over many locations. One reason the U.S. DoD root nameserver was affected by the latest attack was because it doesn’t use anycast, so the entire attack on it went to one single location.
Decentralization has always been central (no pun intended) to the workings of the Internet. It even extends to the software and hardware used by the different entities managing the root nameservers. Since a large variety of operating systems, DNS software, and hardware configurations are used, this has basically removed the risk of any one hardware or software bug affecting all root nameservers at once.
Is it safe?
The failure of this latest attack proves that the root nameservers themselves are an extremely hard target to bring down. That said, there is still a risk that someone, somewhere, will figure out a way to effectively attack and crash them all or at least cause considerable damage. It’s the punch you don’t see coming that knocks you out.