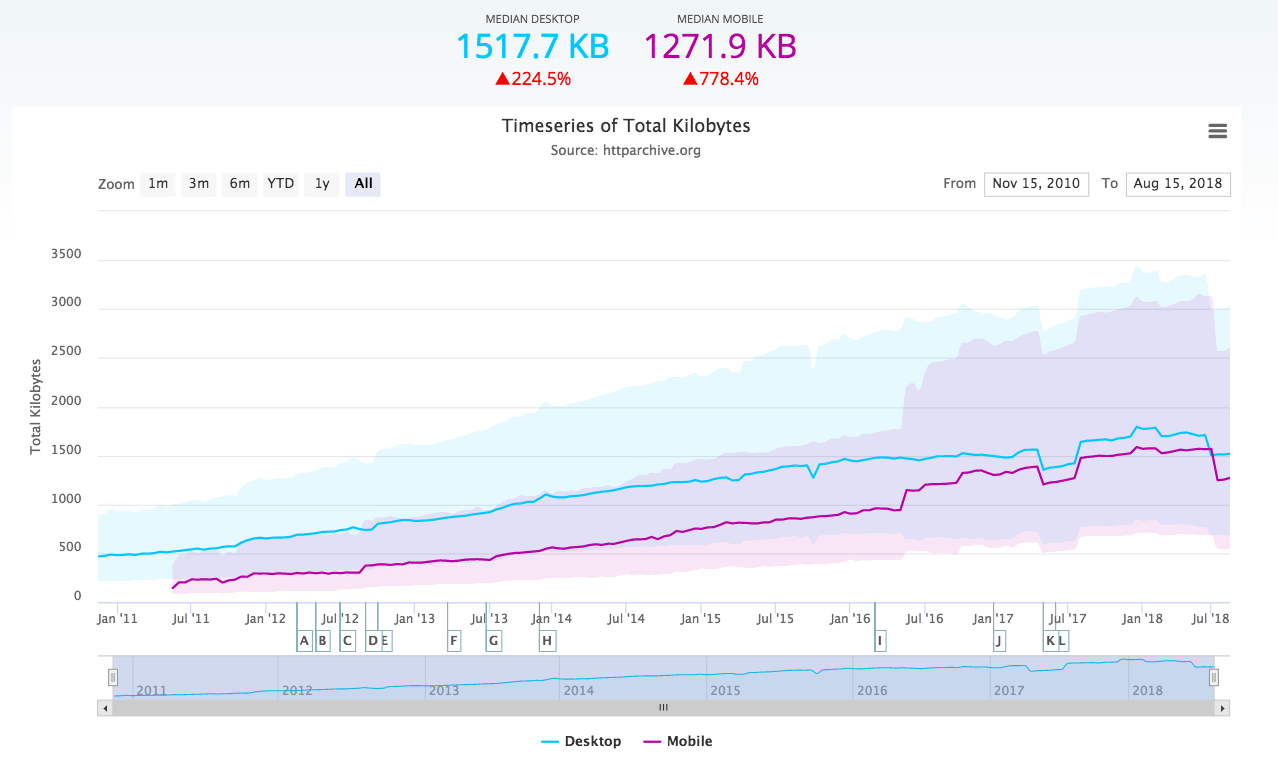
Swedish hosting provider Binero has announced that it has DNSSEC-signed all of its customers’ .se domains. This brings the total amount of signed .se domains to more than 100,000 from the previous total of 5,000.
Swedish hosting provider Binero has announced that it has DNSSEC-signed all of its customers’ .se domains. This brings the total amount of signed .se domains to more than 100,000 from the previous total of 5,000.
“Nearly one in ten Swedish domains are now validated against attacks with manipulated dns-information, like phishing,” Binero’s press release said.
It’s hard to find any worldwide numbers to compare to but ICANN reported yesterday that 88 TLDs (Top-Level Domains) are DNSSEC signed.
But what is DNSSEC (Domain Name System Security Extensions) and why should you care whether your domains are signed with it or not?
DNS was created in an era when the Internet was a bit friendlier
We spoke to the guys at Atomia, a Swedish company providing a high-performance hosting and server automation platform, about exactly those issues.
Pingdom: What is DNSSEC?
Atomia: DNSSEC stems from some of the problems that DNS has had for many years. It’s a good catalogue service for relatively small amounts of data – things like IP addresses – but DNS was created in an era when the Internet was a bit friendlier.
There’s not much security built in to the DNS system we have been using so it’s open – it’s not encrypted and there’s nothing to certify where data comes from, who is the sender of a piece of information. If you’re connecting to www.pingdom.com there’s no way of verifying that the DNS data you get back, which your computer needs to be able to connect to your site, is the true data and that it hasn’t been compromised.
Normally when you browse to a site, your computer sends a question to a DNS resolver, which checks the public catalogues that are DNS for the domain. If it’s pingdom.com you browse to, the resolver then checks with the DNS root server that handles .com domains, and then the one that handles pingdom.com specifically. Eventually it gets an IP address that is then sent back to your computer and the browser connects.
In that scenario it’s then quite possible that someone in the middle captures the request from your computer and returns a fake IP. It could possibly even look like the site you wanted to connect to but it’s not the real thing. This is usually referred to as DNS cache poisoning.
And that’s the problem that DNSSEC tries to address.
Pingdom: Sounds like it works the same way like if we were to digitally sign an email before sending it.
Atomia: Exactly the same, except DNSSEC only deals with signing the information, whereas solutions for securing email often also supports encryption.
Pingdom: It seems like DNSSEC was first discussed and developed in the mid to late 1990s. Why has it taken so long to be put into actual use?
Atomia: Well, first of all DNS is a rather critical infrastructure so we’ve been very careful not to upset anything that works. It’s also a bit like the chicken or the egg: for there to be any use for DNSSEC we need a number of zones to be certified and that the Internet operators’ resolvers validate the domain data. Alternatively, the Internet client applications, like web, email, chat, etc. could validate the data. So it’s like everybody has been waiting for everybody else to do something, passing the buck, if you like.
Then some have said that the root, the bottom of the DNS tree, which is handled by a U.S. organization, has not been signed so why should we worry about it? [The first gTLD signed was .org in 2009] Other top-level domains like .com and .net came later and now it’s all starting to roll.
In Sweden we’ve had a head start since .SE [the organization responsible for the .se domain] and the Swedish Internet operators have been involved and almost all operators now validate the signing of domains.
But it’s still been quite few domains that have been signed, at least until now, when Binero has signed all domains it hosts.
Pingdom: So this is something that is rolling out across the world now?
Atomia: Yes, it is, but ever so slowly. The big top-level domains have DNSSEC now and many country domains as well. There are still many who don’t support it yet, mostly for country-specific domains.
Pingdom: As a typical SME with a domain and a website, is this something you should care about?
Atomia: The slow rollout shows that it’s tough to get people to care about this, it’s not something they immediately think about and put time into, especially when they see that not many others are doing it.
Then it’s hard to see the value.
But anyone that has a domain should check with their registrar and provider to see if they support DNSSEC. A bit of push from customers will probably make providers move a bit faster.
Pingdom: What is the natural extension of DNSSEC, what will come next?
Atomia: So we have this system, DNS that has worked well for 30 years or more and DNSSEC is rolling out over the world. If you could add to that system that you can trust the system in the same way we trust SSL sites, then you can start looking at adding more information. We trust SSL for trade in billions per day and if we can trust DNS in the same way things can get interesting.
If you can say “this certificate is valid for my website” you can tell customers who want to connect to www.pingdom.com, which certificate they should trust. Basically you won’t need a third party other than the DNS root.
Today browsers have lists of Certificate Authorities and that responsibility can be transferred to individual administrators. So the result would be increased flexibility and less cost, and that’s something we see happening now, since about a year or so.
DNSSEC is coming – get ready
We’d like to say a big thank you to Atomia for setting us straight with regards to DNSSEC.
Although it may not be a topic you’ve had to deal with before, get ready, because sooner or later DNSSEC will come your way. Even if the registrar and Internet provider you currently use don’t currently offer DNSSEC signing of domains, you should get in touch with them and see if it’s in their plans.
It seems to us that spreading awareness of DNSSEC and increasing the adoption of this technology can only benefit us all.
After all, better security on the Internet is a good thing, right?
Photo by Ralph Aichinger.